MAKE A MEME
View Large Image
| View Original: | CPT-Internet-DigitalSignatures.svg (670x650) | |||
| Download: | Original | Medium | Small | Thumb |
| Courtesy of: | commons.wikimedia.org | More Like This | ||
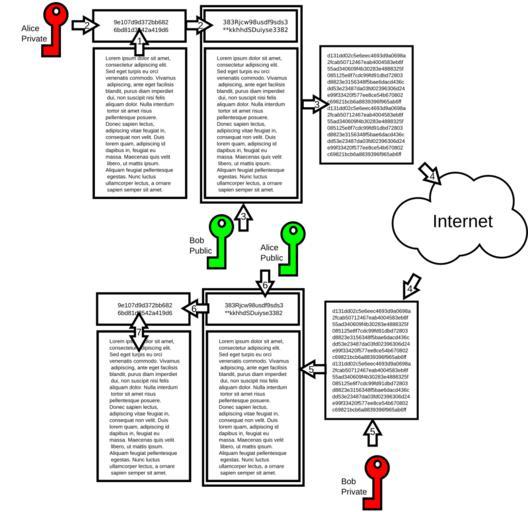
| Keywords: CPT-Internet-DigitalSignatures.svg en How Alice can send a private message to Bob Data is hashed to create message digest Alice's private key is used to encrypt the message digest to create a digital signature The message is appended to the data Bob's public key is used to encrypt the data and signature Encrypted data is sent across the internet Bob receives the data and decrypts the message using his private key Alice's public key is used to decrypt the signature into the message digest The message digest is checked against the original message If they are the same then the message has been sent and received correctly inkscape own Pluke 2011-05-17 Cc-zero Public-key algorithms | ||||